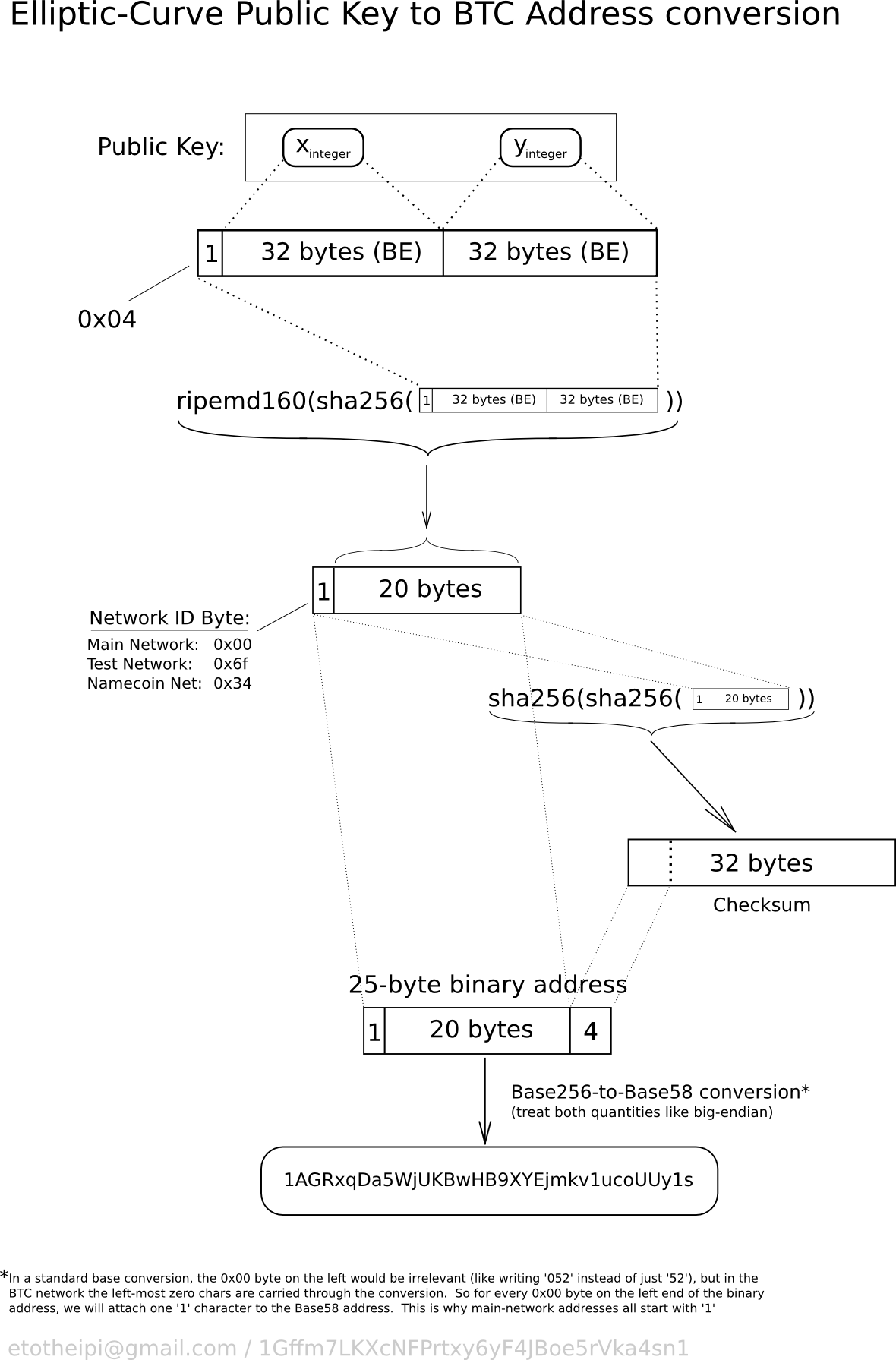
The way Bitcoin checks a public address is using what is called Base58Check. While the Bitcoin Wiki covers Base58Check, I'll outline how it works in both.
Table of contents
Launching Xcode If nothing happens, download Xcode and try again. Latest commit. Git stats 10 commits. Failed to load latest commit information. View code. Validate Bitcoin address Methodology Scripts No-brainer ways. Validate Bitcoin address This is a collection of scripts to validate a bitcoin wallet address. Methodology Check a Bitcoin address for its validity.
- mining bitcoin gold profit calculator?
- rvn btc binance.
- btc exam model paper 2021!
- bitcoin android wallet segwit;
- bitcoin-address-soft-regex-validation - npm package | Snyk.
- bitcoin mining machine specifications!
With this encoding, a bitcoin address encodes 25 bytes: the first byte is the version number, which will be zero for this task ; the next twenty bytes are a RIPEMD digest, but you don't have to know that for this task: you can consider them a pure arbitrary data ; the last four bytes are a checksum check. They are the first four bytes of a double SHA digest of the previous 21 bytes. Scripts Golang Ruby PHP Some key facts about valid Bitcoin addresses: A Bitcoin address is between 25 and 34 characters long; the address always starts with a 1; an address can contain all alphanumeric characters, with the exceptions of 0, O, I, and l.
License MIT. Security Policy No. Commit Frequency. Open Issues 0. Open PR 3.
Mastering Bitcoin by
Last Release 2 years ago. Last Commit 5 months ago. Code of Conduct No. Funding No. Age 2 years. Dependencies 0 Direct. Versions 7. Install Size kB.
- james dyson bitcoin?
- man lost millions in bitcoin.
- Your comment on this question:.
- - Cryptocurrency address generator and validator (v)?
- Bitcoin address.
- Please click one of the tools below:.
Dist-tags 1. Maintainers 1. TS Typings Yes. Readme Versions 7. Last but not least: it's written in TypeScript. What is bitcoin-address-soft-regex-validation? Is bitcoin-address-soft-regex-validation popular? Is bitcoin-address-soft-regex-validation safe to use? Is bitcoin-address-soft-regex-validation well maintained? Everything else in the HD wallet is deterministically derived from this root seed, which makes it possible to re-create the entire HD wallet from that seed in any compatible HD wallet.
This makes it easy to back up, restore, export, and import HD wallets containing thousands or even millions of keys by simply transferring only the root seed. The root seed is most often represented by a mnemonic word sequence , as described in the previous section Mnemonic Code Words , to make it easier for people to transcribe and store it. The process of creating the master keys and master chain code for an HD wallet is shown in Figure The root seed is input into the HMAC-SHA algorithm and the resulting hash is used to create a master private key m and a master chain code.
The chain code is used to introduce entropy in the function that creates child keys from parent keys, as we will see in the next section. Hierarchical deterministic wallets use a child key derivation CKD function to derive children keys from parent keys. The chain code is used to introduce seemingly random data to the process, so that the index is not sufficient to derive other child keys.
Thus, having a child key does not make it possible to find its siblings, unless you also have the chain code. The initial chain code seed at the root of the tree is made from random data, while subsequent chain codes are derived from each parent chain code. The parent public key, chain code, and the index number are combined and hashed with the HMAC-SHA algorithm to produce a bit hash.
The resulting hash is split into two halves.
Bitcoin address: Create, Get example, Format – BitcoinWiki
The right-half bits of the hash output become the chain code for the child. The left-half bits of the hash and the index number are added to the parent private key to produce the child private key. Changing the index allows us to extend the parent and create the other children in the sequence, e. Each parent key can have 2 billion children keys. Repeating the process one level down the tree, each child can in turn become a parent and create its own children, in an infinite number of generations.
Child private keys are indistinguishable from nondeterministic random keys. Because the derivation function is a one-way function, the child key cannot be used to find the parent key. The child key also cannot be used to find any siblings. Only the parent key and chain code can derive all the children.
Without the child chain code, the child key cannot be used to derive any grandchildren either.
You need both the child private key and the child chain code to start a new branch and derive grandchildren. So what can the child private key be used for on its own? It can be used to make a public key and a bitcoin address. Then, it can be used to sign transactions to spend anything paid to that address. A child private key, the corresponding public key, and the bitcoin address are all indistinguishable from keys and addresses created randomly.
The fact that they are part of a sequence is not visible, outside of the HD wallet function that created them. As we saw earlier, the key derivation function can be used to create children at any level of the tree, based on the three inputs: a key, a chain code, and the index of the desired child. The two essential ingredients are the key and chain code, and combined these are called an extended key.
Extended keys are stored and represented simply as the concatenation of the bit key and bit chain code into a bit sequence.
There are two types of extended keys. An extended private key is the combination of a private key and chain code and can be used to derive child private keys and from them, child public keys. An extended public key is a public key and chain code, which can be used to create child public keys, as described in Generating a Public Key. Think of an extended key as the root of a branch in the tree structure of the HD wallet.
With the root of the branch, you can derive the rest of the branch. The extended private key can create a complete branch, whereas the extended public key can only create a branch of public keys. An extended key consists of a private or public key and chain code. An extended key can create children, generating its own branch in the tree structure.
Sharing an extended key gives access to the entire branch. Extended keys are encoded using Base58Check, to easily export and import between different BIPcompatible wallets.
Popularity
Because the extended key is or bits, it is also much longer than other Base58Check-encoded strings we have seen previously. As mentioned previously, a very useful characteristic of hierarchical deterministic wallets is the ability to derive public child keys from public parent keys, without having the private keys. This gives us two ways to derive a child public key: either from the child private key, or directly from the parent public key.
An extended public key can be used, therefore, to derive all of the public keys and only the public keys in that branch of the HD wallet structure. This shortcut can be used to create very secure public-key-only deployments where a server or application has a copy of an extended public key and no private keys whatsoever. That kind of deployment can produce an infinite number of public keys and bitcoin addresses, but cannot spend any of the money sent to those addresses. Meanwhile, on another, more secure server, the extended private key can derive all the corresponding private keys to sign transactions and spend the money.
One common application of this solution is to install an extended public key on a web server that serves an ecommerce application. The web server can use the public key derivation function to create a new bitcoin address for every transaction e. The web server will not have any private keys that would be vulnerable to theft.